For enterprises, the stakes are high. A single prompt injection or model compromise can expose sensitive data, intellectual property, or regulated information, triggering not only operational disruptions but also regulatory penalties and reputational damage. With global frameworks like the EU AI Act, NIST AI RMF, and ISO/IEC 42001 setting higher standards for transparency and accountability, securing generative AI has shifted from a technical concern to a boardroom priority.
Recent data shows the risk is real. IBM reported 13% of organizations already faced AI model breaches, with most lacking access controls. Palo Alto Networks noted a 890% surge in GenAI traffic, with 10% of applications rated high risk.
Key Takeaways
- Generative AI security (Gen AI security): Protects AI models, data, and outputs from misuse.
- New risks: Data leakage, prompt injection, model theft, misinformation, and compliance gaps.
- Best practices: Governance, guardrails, data protection, infrastructure hardening, human oversight.
- Implementation focus: Embed AI security services early in AI workflows.
- Monitoring & response: Use logging, red-teaming, and GenAI-specific incident playbooks.
- Future outlook: More regulation, stronger defenses, and support from Generative AI Development Companies.
This guide explains the security risks associated with generative AI, details how to safeguard GenAI applications using proven frameworks, outlines best practices for securing generative AI, and demonstrates how AI security services and expert AI Development Services help enterprises build secure and compliant systems.
Let’s dive into it.
What is Generative AI Security?
Generative AI security is the practice of ensuring confidentiality, integrity, and responsible use of GenAI systems. It covers the protection of models, training pipelines, and generated outputs against manipulation, misuse, or data exposure.
Shared Responsibility Model
Defense is divided. Vendors secure infrastructure, base models, and cloud environments. Enterprises must secure prompts, fine-tuning, and governance, ensuring policies and controls are enforced across the AI lifecycle.
Core Security Risks of Generative AI
Generative AI introduces attack vectors that traditional security frameworks do not fully address. Data may leak through outputs, models can be reverse-engineered, and unauthorized deployments multiply the attack surface. These security risks of generative AI demand proactive defense strategies across every stage of the AI lifecycle.
Data & Model Vulnerabilities
Data pipelines and model structures form the foundation of GenAI, but they remain open to exploitation. Without proper safeguards, Gen AI data security is weakened, creating both operational risks and regulatory exposure.
-
Sensitive data disclosure — Personal or regulated information may surface in model outputs or remain stored in training data.
-
Training data poisoning — Malicious entries placed in datasets can alter model behavior and reduce reliability.
-
Model theft/extraction — Adversaries can mimic model functions through repeated queries, thereby stealing intellectual property and reducing a competitor's strength.
-
Overfitting & proprietary algorithm leakage — Inadequate training may reveal internal logic, exposing trade secrets to outside parties.
Misuse & Malicious Attacks
Threat groups are adapting GenAI as a weapon. The same systems that draft useful text or code can also be turned toward fraud, malware, and large-scale social engineering. The speed and scale of output give attackers an advantage that older tools never offered.
-
Prompt injection & jailbreaks — Well-crafted prompts can cut around guardrails, making a model disclose protected information or ignore built-in controls.
-
Deepfakes & misinformation — Generated voices, text, and images are already being used to spread false stories, damage reputations, and influence opinion.
-
AI-generated phishing / malicious code — GenAI can assemble convincing phishing emails and exploit-ready code in minutes, raising both volume and effectiveness of attacks.
Operational & Governance Risks
Some of the biggest gaps show up not in the models, but in how they are used. Weak oversight and scattered responsibility often leave systems exposed. When staff run tools without approval or when a business leans too heavily on third parties, control slips away.
-
Shadow AI / Uncontrolled Deployments — Employees bring in GenAI tools independently, disregarding company rules and creating blind spots for security teams.
-
Supply chain dependencies — Outside APIs, pre-trained models, and datasets can carry flaws that the organization cannot easily detect or fix.
-
Denial-of-Service (DoS) targeting models — Flooding a model with queries can choke performance, knock services offline, or delay critical operations.
-
Excessive autonomy — Agents given too much freedom may act outside intended limits, leading to mistakes that damage both operations and reputation.
Compliance & Ethical Risks
Rules around AI are tightening. Europe has its AI Act. The U.S. leans on NIST and sector laws like HIPAA. Regulators everywhere want the same thing: accountability and clear records. Companies that can’t show that they can't face fines, lawsuits, and damage that can’t be easily repaired.
-
Navigating GDPR, HIPAA, EU AI Act, NIST AI RMF — Each framework demands proof that data is handled lawfully and that decisions can be explained.
-
Accountability & explainability gaps — Black-box systems don’t give clear answers, which makes audits messy and security investigations harder.
-
Bias, discrimination & fairness issues — Bad training data leads to unfair results. That means lawsuits, lost trust, and products that may be pulled from the market.
How to Safeguard Generative AI Applications
Securing Generative AI isn’t solved with one tool or a single layer of defense. What works is structure: a clear governance model, tested controls, and day-to-day discipline in how systems are built and used. Miss any one of these, and the whole security effort starts to weaken.
1 Establish a Robust Governance Framework
Governance is the foundation. If a company doesn’t know what models it runs or where the data comes from, the rest of the security program will always be patchwork.
-
AI Bill of Materials (AI-BOM). The starting point is visibility. Many firms can’t list the models or datasets they rely on. An AI-BOM is simply a record: models, data sources, APIs, outside components. It’s not alluring, but when an incident happens, this inventory becomes the only way to trace back what went wrong.
-
Policies and Roles. Once there’s a record, rules must follow. What can and cannot be done with GenAI should be written down, not left to guesswork. Someone needs to own each risk, and there has to be a clear path for escalation. In practice, this cuts down confusion when incidents occur.
-
Frameworks. Policies on their own can be vague. That’s where standards help. NIST AI RMF, ISO/IEC 42001, and the OWASP LLM Top-10 take broad concerns and turn them into steps that security teams can actually enforce.
Governance connects these pieces. The inventory tells you what exists. Policies define how it may be used. Frameworks ensure that rules are applied consistently across projects and business units.
2. Generative AI Security Best Practices
Good governance is only a start. Absolute protection comes from controls that are actively used in daily operations. The following are widely seen as best practices for generative AI security that regulators and auditors now expect.
-
Access controls and RBAC. Limit who can fine-tune, query, or deploy a model. Without strict roles, sensitive operations end up in the wrong hands. Many GenAI breaches have started here.
-
Prompt filtering and input/output validation. Every prompt should be screened before the model sees it. And every response should be checked before it goes out. This is the only reliable way to stop prompt injection at scale.
-
Guardrails and external classifiers. Internal checks fail. Extra filters catch what the core model misses—harmful outputs, policy violations, or unsafe requests.
-
Data encryption, anonymization, and differential privacy. Encryption is obvious, but still unevenly applied. Anonymization and privacy techniques reduce the risk of exposing sensitive records during training or inference.
-
Bias and fairness audits. Bias creeps in through training data. Regular audits help identify these issues before they appear in production and are a core part of AI safety best practices.
This is as much about compliance as it is about protecting business reputation.
Each of these controls closes off a known attack path—whether it’s data leakage, malicious prompts, or biased outputs. Together, they form a practical defense-in-depth strategy.
3. Implementation Considerations
Even the best rules and controls fail if they are not applied in everyday work. That’s why AI implementation must include security from the ground up.
-
Secure workflows from data collection to deployment. Every stage needs checks: validation, encryption, and monitoring. If risks are not addressed early, they carry straight into production.
-
Zero-Trust architecture for GenAI environments. No request should be trusted by default. Strong authentication and network segmentation block unauthorized access.
-
Supply chain vetting of APIs, models, and open-source components. Third-party parts often carry hidden risks. Vetting is slow work, but it prevents costly surprises later.
-
Embedding AI security services into the AI implementation lifecycle. Specialized teams or partners bring expertise most organizations lack. They harden deployments, test defenses, and keep compliance on track.
-
Human-in-the-loop validation for sensitive outputs. Not every result should be automated. In areas such as healthcare or finance, manual review helps protect against costly errors.
-
Staff awareness and training. The best controls fail if employees don’t understand them. Training staff to recognize biased outputs, hallucinations, and misuse turns the workforce into part of the defense system.
When governance, best practices, and careful AI implementation are in place, GenAI shifts from being a source of unmanaged risk to a controlled business capability.

Monitoring, Testing & Incident Response
Security does not stop once a GenAI model is deployed. Systems must be watched, tested, and prepared for failure. Many of the most damaging breaches in AI come not from missing controls, but from missed signals. A monitoring and response program keeps minor flaws from turning into business-wide incidents.
Continuous Monitoring & Logging
Every interaction with a model leaves a trace. Capturing those traces is the only way to spot misuse or drift before damage spreads.
-
Track all model interactions. Requests and outputs should be logged in detail. This creates an audit trail that investigators can use if data is leaked or a model is abused.
-
Behavioral analytics to detect drift or misuse. Static logs are not enough. Analytics systems can flag unusual traffic, changes in response patterns, or signs of prompt manipulation. These signals give security teams time to act and help ensure defenses remain reliable over time.
Testing & Validation
Controls need constant proof that they work. GenAI models respond in unpredictable ways, so ongoing validation is not optional.
-
Adversarial testing and red-teaming. Internal teams, or outside specialists, must simulate attacks like prompt injection or training data poisoning. This shows where defenses fail in practice and strengthens operational resilience.
-
Specialized tools. Platforms such as Microsoft PyRIT, IBM’s AI Risk Toolkit, and MITRE ATLAS give structure to this testing. They document methods, results, and countermeasures, helping teams avoid blind spots and maintain confidence in deployed systems.
Incident Response for GenAI
Even with monitoring and testing, some attacks succeed. A fast response limits the damage. Traditional playbooks help, but GenAI introduces unique failure modes that demand their own procedures.
-
GenAI-specific playbooks. Response plans must cover data leakage through outputs, prompt injection that changes model behavior, and model compromise.
-
Automated response and containment. Systems should be able to pause access, isolate affected components, or roll back models when threats are confirmed. Waiting for manual approval often takes too long.
-
Forensic logging for compliance. Detailed logs are essential for regulators and for rebuilding trust. Without them, proving due diligence after an incident is almost impossible.
Tools & Techniques for Gen AI Security
Governance and policies set the ground rules, but they don’t stop an attacker. Day-to-day protection depends on practical tools. These aren’t silver bullets, but they make the difference between a system that bends and one that breaks.
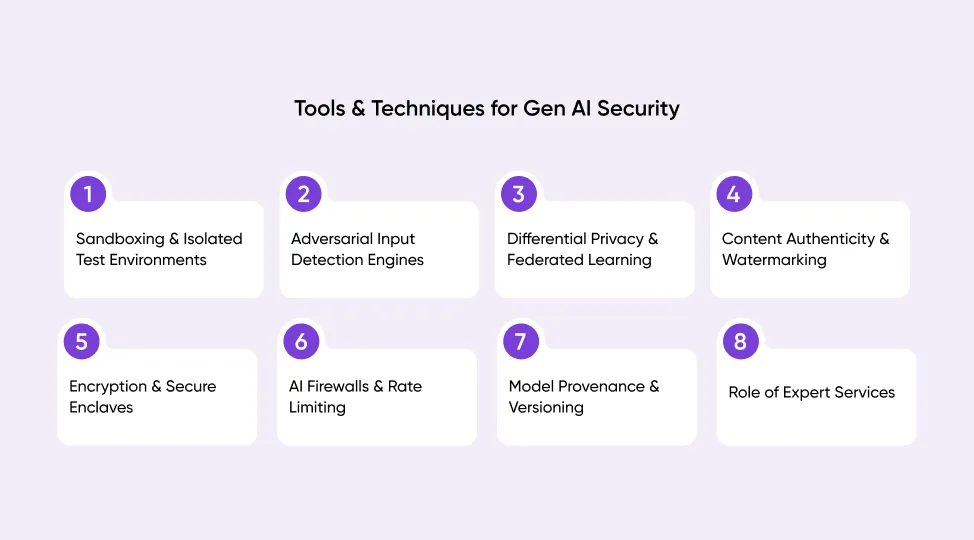
Sandboxing & Isolated Test Environments
You don’t throw a new model straight into production. It gets tested first. A sandbox is where unsafe prompts and strange outputs are caught before real users see them. Many firms skip this step, and that’s where trouble begins.
Adversarial Input Detection Engines
Attackers don’t always go head-on. They write clever prompts that slip around safety rules. Detection engines look for those patterns. They don’t block everything, but they stop a good share of injection attempts before damage is done.
Differential Privacy & Federated Learning
Data remains one of the most exposed assets in GenAI. Differential privacy masks individual records so they cannot be re-identified from outputs. Federated learning distributes training across multiple nodes, keeping raw data local. Combined, these methods limit the fallout of a single breach and reduce systemic exposure.
Content Authenticity & Watermarking
AI outputs need proof of origin to meet compliance and audit demands. Watermarking adds cryptographic markers inside generated text, images, or audio. Authenticity tools extend this by logging metadata on how and when content was produced. These measures are essential in sectors such as media, finance, and healthcare, where manipulated data can cause significant harm.
Encryption & Secure Enclaves
Encryption is the baseline. Everyone knows it. However, many still fail at the basics—such as data left unencrypted at rest or weak keys. Secure enclaves push further: computations happen in sealed-off environments. Attackers can’t tamper with what they can’t reach. These protections strengthen gen AI data security by limiting exposure of sensitive training records and system outputs.
AI Firewalls & Rate Limiting
Think of this as the gatekeeper. The firewall screens traffic before it touches the model. Unsafe queries get blocked, abusive users get throttled. Adding rate limiting and denial-of-service attacks makes them far less effective.
Model Provenance & Versioning
Every model needs a history. Versioning lets teams track what was deployed and when. Provenance ties an output back to a specific release. When an incident occurs, that trace is often the only way to explain what went wrong.
Role of Expert Services
Not every company has the depth to run these defenses well. A Generative AI Development Company provider brings experience that shortens the learning curve. AI security services keep systems under watch when in-house teams are stretched thin.
Practical help usually looks like this:
- Hardened pipelines are built securely from the start.
- External red-team exercises to test defenses.
- Compliance guidance for frameworks like NIST, ISO, HIPAA, or the EU AI Act.
- Continuous monitoring of drift, misuse, and anomalies.
- Incident response backup when a breach overwhelms internal staff.
These services don’t replace internal security teams. They extend them. For many enterprises, that’s the difference between scaling GenAI safely and becoming the next breach headline.
Organizational Framework for GenAI Security
Technology alone doesn’t hold the line. Security breaks down when people and processes don’t keep up. A framework for Gen AI security must encompass policy, ownership, and accountability across the entire business.
Security Policies for AI Models
Every enterprise already has security policies for networks and data. GenAI needs the same. Policies should set clear rules for model usage, fine-tuning, and acceptable data. Without this baseline, teams will improvise, and that usually ends badly.
Cross-Functional Ownership
GenAI isn’t just an IT problem. Developers, security staff, compliance officers, and even legal teams all play a role. Risk doesn’t live in one department. If ownership is split or unclear, gaps appear, and attackers find them quickly.
Risk & Ethics Committees
Technology decisions can’t be left to engineers alone. Risk and ethics committees review how models are trained, tested, and used in production. They also track bias, explainability, and compliance exposure. These groups act as a second set of eyes before something goes live.
Partnerships with Expert Providers
Most companies won’t build all defenses in-house. An AI Development Services provider can fill skill gaps. These partners handle secure pipeline design, compliance audits, or continuous testing. They also provide AI security services, such as red-teaming and incident support. For many firms, that outside help makes the difference between a policy on paper and security in practice.
Strengthening Current Systems & Preparing for What’s Ahead
GenAI security isn’t only about what’s coming next—it’s also about fixing what’s already in place. Enterprises need a two-track approach: strengthen current systems with practical steps, and prepare for the advanced threats and regulations that are just ahead.
Part A: Strengthening Current GenAI Systems
Most firms already use GenAI tools in production. Rebuilding from scratch is costly, but reinforcing existing systems is both faster and effective.
-
Audit What You Have
Start with visibility. Inventory all models, datasets, APIs, and tools. Many companies discover unapproved deployments or outdated controls during this process.
-
Tighten Access and Data Controls
Restrict who can fine-tune or deploy models. Review logs. Encrypt and anonymize sensitive data, even in internal use. These measures close common leak points.
-
Add Monitoring Where It’s Missing
Many systems run with little oversight. Add logging and analytics to catch unusual activity, model drift, or spikes in requests. Even partial monitoring improves response time.
-
Test with Adversarial Methods
Use red-teaming to stress-test live systems against hostile prompts. Tools such as Microsoft PyRIT or MITRE ATLAS help simulate attacks and identify weak spots.
-
Bring in Outside Support
An AI Development Services provider can review deployed systems, patch design flaws, and deliver AI security services, such as compliance audits or continuous monitoring.

Part B: Emerging Trends & Future Outlook
While current systems are being secured, the horizon is shifting fast. Enterprises must prepare for new threats, evolving rules, and next-generation defenses.
- Advanced Threats
Beyond prompt injection, expect model inversion, uncontrolled AI agents, and a deepfake surge that makes fraud more challenging to detect.
- Regulatory Evolution
The EU AI Act, US AI Bill of Rights, NIST frameworks, and ISO/IEC standards are tightening global requirements. Penalties and reputational risks for non-compliance will rise.
- Next-Generation Security Solutions
New tools are emerging: AI-native firewalls that inspect prompts in real time, self-defending systems that adapt under attack, and zero-trust frameworks designed for AI workloads. Currently in an early stage, but likely to become standard in large-scale deployments.
What Leaders Should Do Next
Generative AI is no longer experimental. It powers banks, hospitals, e-commerce, and government systems, but with that scale comes risk. Data leaks, poisoned inputs, and prompt abuse are hitting enterprises already, and regulations are tightening. Strong defenses require more than piecemeal controls, and leaders must follow AI safety best practices to stay ahead. Governance, monitoring, tested guardrails, and resilient workflows must be built into every stage of deployment.
Internal security teams provide the baseline, but few organizations can manage the complexity alone. Partnering with a trusted Generative AI Development Company gives structure for long-term adoption, governance, and lifecycle management. Enterprises that act now will reduce their exposure, remain compliant, and maintain trust in their AI programs. Those who delay will face rising costs and more sophisticated threats that are harder to contain.
Tags
Generative AI Best Practices
Generative AI development
Generative AI consulting
Generative ai



 Facebook
Facebook
 Twitter
Twitter
 LinkedIn
LinkedIn
 Pinterest
Pinterest