Technology


8 min


Cyber warriors! Ready to dive into the latest cybersecurity trends? From cutting-edge innovations to robust protection strategies, we've got you covered. This blog will explore how the cybersecurity landscape is evolving, from AI-powered threat detection to zero-trust security architectures. It's time to level up your cybersecurity game and keep those digital threats at bay!

By Anupam Singh
14 Feb, 2024
In today's digitally driven world, businesses of all sizes and governmental entities rely heavily on computerized systems to streamline operations & activities. However, this unprecedented level of connectivity exposes them to a myriad of cyber threat trends. It makes cybersecurity a critical priority in safeguarding sensitive data and preventing unauthorized access. Cyber-attacks will cost the global economy over $10.5 trillion by next year's end. This figure underscores the critical importance of cybersecurity, demanding strategic attention and investment at every level – individual, organizational, or governmental.
Nevertheless, companies encounter a dynamic cyber threat as threat actors become more sophisticated, fueled by advancements like AI. Technological innovation and evolving business requirements have expanded the attack surface with new environments, devices, and software. Therefore, we have come up with current or emerging cybersecurity trends in 2024 to protect businesses.
Before discussing cybersecurity industry trends, let's briefly familiarize ourselves with the latest cybersecurity attacks or threats.
In 2024, the cybersecurity generation is fraught with an array of evolving threats that are making headlines worldwide. From sophisticated ransomware attacks targeting critical infrastructure to insidious phishing schemes aimed at stealing sensitive data. Let’s explore a few trending or happening threats:-
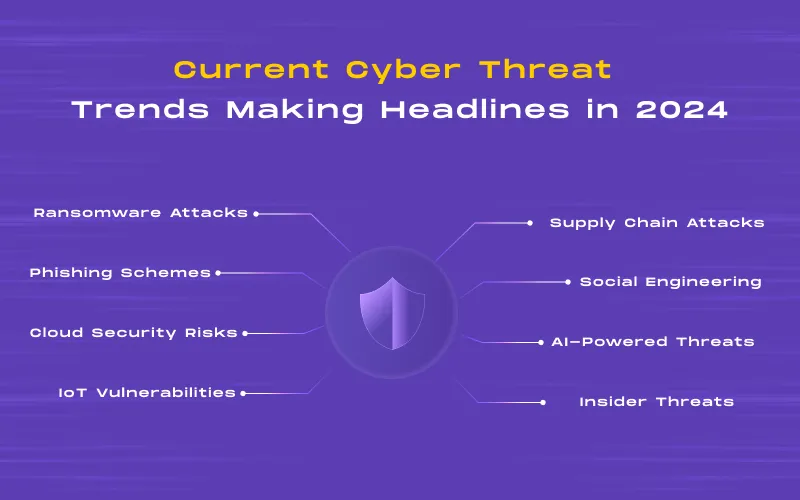
Ransomware Attacks: Sophisticated ransomware attacks are on the rise, targeting critical infrastructure and organizations of all sizes. These attacks often involve encrypting sensitive data followed by ransom demands for release. As per report- In 2021, a staggering 623.3 million ransomware attacks ravaged global networks. Additionally, 236.1 million attacks in just the first half of 2022. It highlights the alarming escalation of cyber threats worldwide.
Phishing Schemes: Insidious phishing schemes continue to pose a significant threat, with cybercriminals using deceptive tactics to trick individuals into divulging sensitive information such as login credentials or financial details. Therefore, it became essential to stay updated & keep our business protected by assuring the latest cybersecurity trends in 2024.
Cloud Security Risks: As organizations increasingly rely on cloud-based services, the security of cloud environments becomes paramount, with potential risks including data breaches, misconfigurations, and unauthorized access.
Internet of Things (IoT) Vulnerabilities: The proliferation of IoT devices has expanded the attack surface, providing cybercriminals with new entry points to infiltrate networks & compromise security.
Supply Chain Attacks: Cybercriminals increasingly target supply chains to infiltrate networks and compromise data integrity. It highlights the interconnected nature of modern business ecosystems.
Social Engineering Tactics: Cybercriminals continue to employ social engineering tactics, such as pretexting and baiting, to manipulate individuals into disclosing sensitive information or performing actions that compromise security.
AI-Powered Threats: Using artificial intelligence by cybercriminals introduces new challenges as AI-driven attacks become more sophisticated and difficult to detect. It requires advanced defense mechanisms to mitigate their impact.
Insider Threats: Insider threats, whether intentional or accidental, remain a significant concern, as employees with access to sensitive information pose a risk of data theft, sabotage, or accidental exposure of confidential data.
Explore the cutting-edge advancements and proactive strategies shaping today's cybersecurity industry trends. From AI-driven defense mechanisms to the rise of quantum-resistant encryption. Let’s discover-
AI and ML Services revolutionize cybersecurity, empowering defenders with advanced analytics and automation capabilities. Machine learning algorithms analyze vast datasets to detect anomalies and predict potential threats in real-time. It helps in enhancing incident response and reducing the burden on human operators. From threat detection to behavioral analysis, AI-driven defense mechanisms are reshaping the landscape and becoming top cybersecurity trends in 2024. It helps businesses with proactive protection against evolving or current cyber threat trends.
 There must be more than the traditional perimeter-based security model in an era of heightened cyber threats. Zero Trust Architecture (ZTA) adopts a "never trust, always verify" approach. It requires continuous authentication and strict access controls to mitigate the risk of insider threats and lateral movement by attackers. By segmenting network resources & enforcing least privilege access, ZTA minimizes the attack surface and enhances overall resilience against cyber threat trends.
There must be more than the traditional perimeter-based security model in an era of heightened cyber threats. Zero Trust Architecture (ZTA) adopts a "never trust, always verify" approach. It requires continuous authentication and strict access controls to mitigate the risk of insider threats and lateral movement by attackers. By segmenting network resources & enforcing least privilege access, ZTA minimizes the attack surface and enhances overall resilience against cyber threat trends.
The emergence of quantum computing presents unprecedented challenges to traditional encryption algorithms, significantly impacting cybersecurity trends in 2024. As quantum computers threaten the security of sensitive data, researchers are racing to develop quantum-resistant encryption schemes capable of withstanding their computational power. Post-quantum cryptography, which includes lattice-based and hash-based algorithms, emerges as a key solution to combat quantum-enabled adversaries. Businesses can ensure the confidentiality and integrity of encrypted communications in a quantum-safe manner by implementing robust encryption methods. It helps address one of the critical current cyber security trends shaping the digital era 2024.
Collaborative threat intelligence sharing enables organizations to proactively identify and mitigate cyber threats by leveraging collective insights and expertise. Information-sharing platforms facilitate the exchange of actionable intelligence, including indicators of compromise (IOCs), attack patterns, and vulnerability disclosures. It helps empower defenders to stay ahead of emerging threats. Threat intelligence sharing enhances situational awareness & strengthens collective defenses against cyber adversaries by fostering collaboration and cooperation among stakeholders.
Cyber resilience, a cornerstone of cybersecurity trends in 2024. It encompasses proactive measures and contingency plans to mitigate the impact of cyber incidents and ensure uninterrupted business operations. Businesses must prioritize robust incident response capabilities in the face of cyber threat trends. It includes timely incident detection, effective containment strategies, and swift recovery procedures. Organizations can avoid emerging threats and minimize disruption to their operations in 2024 and beyond. All it needs to do is align its incident response frameworks with leading industry standards such as the NIST Cybersecurity Framework or ISO 27035.
Endpoint security is undergoing a paradigm shift driven by the rise of remote work and the proliferation of connected devices. As cybersecurity trends in 2024 evolve, traditional antivirus solutions are being augmented or replaced by next-generation endpoint detection and response (EDR) platforms. These platforms leverage advanced behavioral analytics and machine learning to detect and mitigate sophisticated threats across endpoints. Ultimately, helps enhance visibility and control in an increasingly distributed environment.
With the widespread adoption of cloud computing, ensuring the security of cloud environments has become a top priority for organizations. Emerging trends in cyber security in cloud security involve the implementation of robust security controls. It includes data encryption, access management, and continuous monitoring to protect sensitive data and workloads in the cloud. Additionally, adopting cloud-native security solutions and DevSecOps practices enables organizations to build security into their cloud applications and infrastructure from the ground up.
Identity and access management (IAM) is critical in cybersecurity, governing access to resources and safeguarding against unauthorized access. As cybersecurity trends in 2024 evolve, IAM solutions are evolving to incorporate advanced authentication methods, such as biometrics and multi-factor authentication (MFA), to enhance security posture. Additionally, adopting identity governance and privileged access management (PAM) solutions helps organizations enforce least privilege access and mitigate the risk of insider threats.
Threat hunting involves proactively searching for signs of malicious activity within an organization's network and endpoints. As current cyber security trends shift towards proactive defense, threat hunting has emerged as a critical practice for identifying and neutralizing threats before they can cause harm. Threat hunters can uncover hidden threats and vulnerabilities by leveraging threat intelligence feeds and advanced analytics. It enables organizations to respond swiftly and effectively to emerging cyber threats.
In the face of growing cyber threats, cybersecurity awareness and training have become essential components of a comprehensive security strategy. As cybersecurity trends in 2024 emphasize the human element in security, organizations are investing in cybersecurity awareness programs to educate employees about common cyber threats and best practices for protecting sensitive information. By fostering a culture of security awareness, organizations can empower employees to recognize and report potential security incidents, strengthening the organization's overall security posture.
As cyberattacks, online fraud, and IoT usage surge, relying solely on usernames and passwords for authentication becomes obsolete. Enter multi-factor authentication (MFA), a robust solution to prevent security breaches. Users can enhance security and identity verification by deploying MFA systems on smartphones and computers.
The MFA market is projected to hit $34.8 billion by 2028, with a staggering CAGR of 18% from 2024 to 2028.
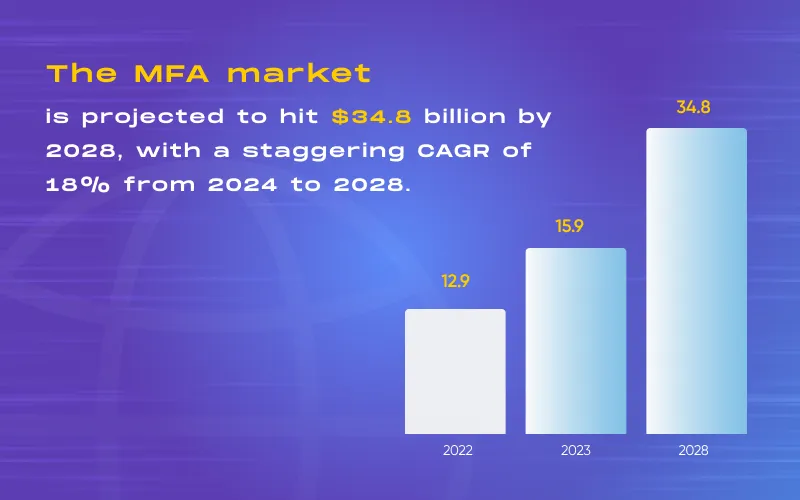
MFA employs multiple validation layers, incorporating diverse factors like login credentials, biometric scans, or one-time passwords. Cloud-integrated solutions enable remote authentication methods such as fingerprint scanning, facial recognition, and document verification. Additionally, risk-based authentication evaluates request-related risks, adding an extra layer of security.
Adopting best practices is crucial for ensuring the protection of digital assets today and in the future. Here are key strategies and methodologies to navigate the complexities of the digital age.
(1.) Multi-Factor Authentication (MFA)
Implement MFA to add an extra layer of security beyond traditional username and password combinations. To enhance identity validation, use biometric verification, one-time passwords, or smart card authentication.
(2.) Zero Trust Architecture (ZTA)
Embrace the Zero Trust model, where trust is never assumed, and verification is required from anyone trying to access resources. Implement strict access controls and continuous authentication to minimize the risk of unauthorized access.
(3.) Continuous Monitoring and Threat Detection
Adopt continuous monitoring tools and advanced threat detection mechanisms to identify anomalies and potential security threats in real time. Proactive monitoring enhances the ability to respond swiftly to emerging cyber threats.
(4.) Employee Training and Awareness
Prioritize cybersecurity awareness training for employees to recognize and mitigate potential threats. Educate staff on social engineering tactics, phishing schemes, and secure online behavior.
(5.) Regular Security Audits and Assessments
Conduct periodic security audits and assessments to identify vulnerabilities in systems and networks. Regular evaluations ensure security measures align with evolving threats and industry best practices.
(6.) Cloud Security Best Practices
If leveraging cloud services, implement robust cloud security measures. Encrypt data, manage access controls and stay informed about the cloud provider's security features to ensure a secure cloud environment.
(7.) Incident Response Planning
Develop a comprehensive incident response plan to manage and mitigate the impact of security incidents effectively. Regularly test and update the plan to address new threats and vulnerabilities.
(8.) Endpoint Security Measures
Strengthen endpoint security with next-generation antivirus solutions, endpoint detection and response (EDR) tools, and device management policies. Secure all devices connected to the network to prevent potential breaches.
(9.) Data Encryption
Implement strong encryption protocols for sensitive data at rest and in transit. Encryption adds a layer of protection, ensuring that even if data is compromised, it remains unreadable without the appropriate decryption keys.
By adhering to these best practices, businesses can establish a proactive cybersecurity posture. It helps safeguard their digital assets today and lays a resilient foundation for the challenges of tomorrow.
Navigating from innovation to protection in cybersecurity demands a proactive approach and a commitment to staying ahead of the curve. By embracing the latest cybersecurity trends in 2024 and implementing best practices, businesses can fortify their defenses against evolving threats and safeguard their digital assets. From harnessing the power of artificial intelligence to adopting zero-trust architectures and prioritizing user awareness, the path to cybersecurity resilience is paved with innovation and vigilance. Let's continue adapting, innovating, and collaborating to secure a safer digital future.
Current cyber security trends include the rise of AI-driven defense, zero trust architecture adoption, and increased focus on cloud security.
Cybersecurity trends for 2023 include advancements in quantum-resistant encryption, enhanced threat intelligence sharing, and further integration of AI into security operations.
Top cybersecurity trends in 2024 may encompass the evolution of endpoint security, increased emphasis on identity and access management, and the continued battle against ransomware and supply chain attacks.
The next big thing in cybersecurity is advancements in quantum computing security, innovations in secure hardware technologies, and developing resilient cyber defense strategies.
What Is an API? A Developer's Guide to Application Integration in 2025
By Dhruv Joshi
5 min read
What Is a Push Notification and Why It Matters for Your App Strategy
By Dhruv Joshi
5 min read
Top React Native Development Companies to Build Scalable Apps
By Dhruv Joshi
5 min read
How Wearable Technology Is Driving Real-Time Data Experiences in Mobile Apps
By Sannidhya Sharma
5 min read

Technology


5 min
What is an API? Learn the real meaning of Application Programming Interfaces in 2025, how APIs work, why they're essential to software development, and how to integrate them. This developer-focused guide breaks down API types, use cases, benefits, and best practices for business success.


Technology


5 min
Wearable technology is reshaping mobile apps with real-time insights, enabling smart alerts, fitness coaching, health monitoring, and more. From smart rings to AR glasses, explore how these evolving devices are creating seamless, personalized experiences across various industries and everyday life.


Technology


5 min
Augmented reality in retail helps brands drive sales and reduce returns by transforming how customers discover, try, and buy products. This blog is your guide to using AR strategically, from choosing the right use cases to launching cost-effective AR experiences that delight customers and differentiate your brand.

Feeling lost!! Book a slot and get answers to all your industry-relevant doubts