IBM’s Cost of a Data Breach Report 2025 puts the global average cost of a breach at $4.44 million. That is only slightly lower than the $4.88 million average in 2024, showing that while detection and response have improved, the financial risks remain significant.
A long-term study of breaches from 2004 to 2024 highlights the same concern. Attacks on web applications and APIs are rising steadily across every industry. Hackers continue to go after login details, personal records, and business data because these credentials are easy to exploit and profitable to sell.
Most organizations still depend on a web application firewall for defense. Traditional WAFs block familiar threats, but they fall short when faced with zero-day exploits, automated bots, or mass credential abuse. They also generate too many false positives and require constant manual updates.
An AI web application firewall addresses these gaps by applying machine learning, deep learning, and predictive analysis. It doesn’t just wait for rules — it learns from traffic, adapts in real time, and strengthens overall app security.
In this write-up, we’ll cover what an AI-powered WAF is, how WAF machine learning improves detection, the features that set it apart, the benefits it brings to businesses, best practices for AI implementation, and how AI security services and AI development services help companies build smarter defenses.
What is an AI-Powered Web Application Firewall?
An AI-powered web application firewall (AI WAF) goes beyond the standard request-and-block model of a traditional firewall. Instead of being limited to signatures and static rule sets, an AI web application firewall processes traffic through trained models that recognize patterns, evaluate anomalies, and adjust decisions automatically. These models use:
- Supervised learning to detect known attack families more accurately
- Unsupervised learning to spot unusual behavior that doesn’t match past data
- Context-aware analysis that looks beyond single requests to evaluate full user sessions
- Predictive scoring that assigns a risk level to each request before it reaches the backend
These methods also play a role in AI in application security testing, helping validate firewalls against both simulated and live attack patterns.
Core Functionality of an AI WAF
An AI WAF is designed to:
- Analyze traffic behavior dynamically – not just by matching signatures, but by learning how normal requests, sessions, and user flows look.
- Apply machine learning WAF models that detect anomalies such as unusual payloads, malformed requests, or sudden spikes in API calls.
- Identify advanced attack patterns, such as SQL injection or cross-site scripting, even when obfuscation or evasion techniques are employed.
- Adapt continuously – models refine themselves as they see more data, so the firewall improves without waiting for manual updates.
- Leverage predictive analysis to anticipate new exploit attempts, helping block zero-day threats before they spread.
Limitations of Traditional WAFs
Rule-based WAFs have done the job for years, but they show cracks in today’s environment:
- Zero-day threats slip through because attackers innovate faster than security teams can update rules.
- Bot swarms and credential stuffing attacks easily bypass static filters.
- High false positives frustrate real users and create friction for DevOps.
- Maintenance burden — large teams spend hours updating signatures, tuning rules, and troubleshooting.
Why AI Is the Next Step
An AI web application firewall tackles these weaknesses with adaptive intelligence:
- Learns from real-time traffic patterns using WAF machine learning models.
- Builds a dynamic baseline of “normal” activity and flags anything unusual.
- Detects zero-day attacks without waiting for signature updates, strengthening overall AI application security.
- Cuts down false positives by distinguishing between genuine and malicious anomalies.
- Continuously adapts, the more traffic it sees, the smarter it becomes.

How AI & Machine Learning Enhance WAF Security
Traditional firewalls work like checklists. They look for rules and block requests that match their criteria. But attackers don’t play by static rules anymore. They hide payloads, change patterns, and launch automated campaigns that a rules-only WAF often misses. This is where AI and machine learning give the firewall sharper eyes.
WAF Machine Learning Models for Pattern Recognition
- Learns what regular traffic looks like by analyzing millions of requests
- Flags anomalies like odd login attempts or strange payloads
- Detects hidden SQL injections and unusual cross-site scripting attempts
- Adapts as apps evolve, keeping pace with changing traffic
AI Implementation for Anomaly Detection & Adaptive Response
- Spots abnormal patterns in real time, without waiting for rule updates
- Adjusts responses based on the severity of the threat
- Blocks high-risk traffic instantly while letting safe sessions continue
- Cuts down false positives that frustrate users and slow down teams
Predictive Threat Analysis with AI
- Uses global intelligence to predict and prepare for new attacks
- Identifies early signs of coordinated campaigns
- Assigns risk scores to sessions, helping prioritize response
- Acts before zero-day exploits spread widely
Continuous Self-Learning Defense
- Models improve every day as they see new traffic data
- No need for constant manual rule updates
- Reduces administrative overhead for security teams
- Builds a stronger defense the longer it runs
These capabilities extend to AI in application security testing, where defenses are validated continuously with simulated traffic and real-world audits.
Key Features of AI Web Application Firewalls
AI-driven WAFs are more than simple filters. They combine detection, analysis, and response in real-time, providing security teams with tools that traditional firewalls cannot match. Below are the key features that set them apart.
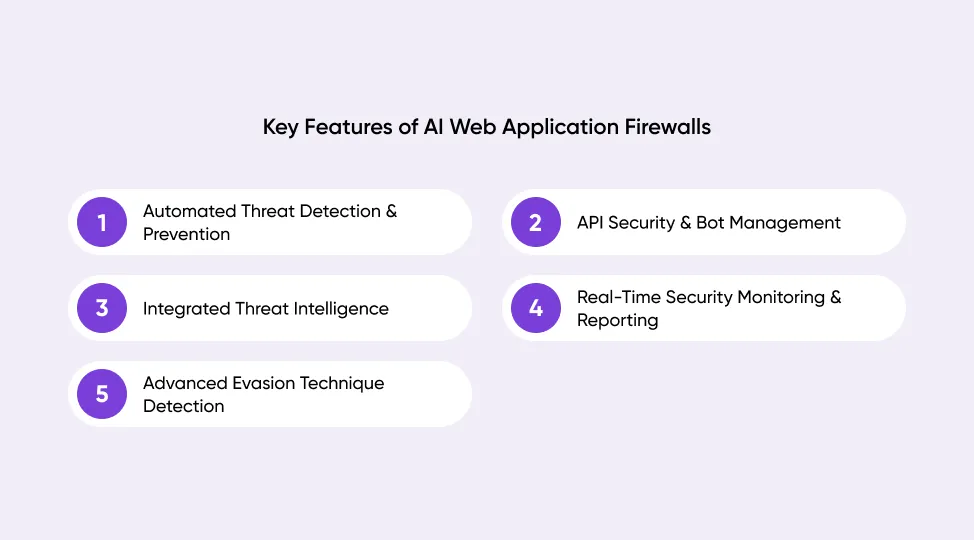
Automated Threat Detection & Prevention
An AI WAF continuously inspects traffic using trained models, not just signatures. This allows it to:
- Catch SQL injections and cross-site scripting even when obfuscated
- Detect DDoS traffic spikes before they overwhelm the system
- Block suspicious requests instantly with minimal false positives, providing effective AI protection for critical applications.
API Security & Bot Management
Modern apps rely on APIs, which attackers often target. AI strengthens API defense by:
- Identifying unusual API calls or excessive request rates
- Blocking credential-stuffing attempts automatically
- Filtering out malicious bots while allowing good bots like search crawlers
Integrated Threat Intelligence
AI WAFs don’t operate in isolation. They connect to global threat feeds and security networks. This means:
- New attack signatures are learned automatically.
- Models adapt quickly to emerging global campaigns.
- Local defenses improve from worldwide intelligence sharing.
Real-Time Security Monitoring & Reporting
Visibility is as important as blocking threats. AI WAFs offer:
- Live dashboards showing traffic patterns and anomalies
- Predictive alerts that warn before incidents escalate
- Detailed logs and forensic reports for compliance and investigations
Advanced Evasion Technique Detection
Attackers often disguise payloads or spread them across vectors. AI helps uncover these tactics by:
- Recognizing polymorphic attacks that constantly change form
- Detecting obfuscation in scripts or encoded payloads
- Correlating multiple small events into a single attack pattern
Real-World Benefits of AI-Powered WAFs
Identify the actual implementation of AI in WAF Web application firewalls within existing systems.
Security Benefits
With AI behind the firewall, protection shifts from reacting after the fact to stopping trouble before it begins. This marks a clear shift toward AI application security, where defenses adapt continuously instead of waiting for manual updates.
- Enhanced Threat Detection: Instead of relying solely on static rules, the system identifies unusual behavior in real-time traffic. It can catch an obfuscated SQL injection or a stealthy XSS attempt that older filters would never notice.
- Reduced False Positives: By learning what normal traffic looks like, the WAF avoids blocking good users. Security teams spend less time digging through “noise” and more time focusing on real threats.
- Automated Security Responses: Attacks don’t wait, and neither does AI. The firewall reacts the moment it sees danger, cutting off risky requests without waiting for someone to tune a rule.
- Zero-Day Attack Protection: Even if the exploit is brand new, AI recognizes behavior that doesn’t fit the baseline. That gives the business a fighting chance to stop an attack no one has seen before.
- Scalability and Performance: Heavy traffic days no longer mean slower apps. The firewall scales with demand, keeping services fast and reliable even during spikes.
Business Impact
The gains go beyond the security team. When AI powers the firewall, the whole organization benefits.
- Lower Operational Costs: Less time wasted on writing rules or fixing false alarms means fewer overtime hours and better use of staff.
- Compliance Support: Meeting PCI DSS, GDPR, or other requirements gets easier with clear reports, accurate logs, and fewer errors. Auditors like clean data, and AI helps deliver it.
- Improved ROI: Working with trusted AI security services yields significant benefits. Breaches cost less when they are stopped early, and the security spend feels justified.
- Customer Trust: Users stay longer and spend more when they feel safe. A strong WAF web application firewall helps build that trust day after day.
- Agility for Growth: As the business expands, the firewall evolves in tandem. Scaling apps doesn’t mean scaling risk, and expansion is smoother when security isn’t holding things back.

AI-Powered WAF vs. Traditional WAF
Application security has moved past simple filters. Today’s defenses need to understand behavior, not just block known signatures.
To better understand how traditional WAFs are upgraded and enhanced with AI, refer to the table below.
| Aspect |
Traditional Web Application Firewall |
AI-Powered Web Application Firewall |
| Detection Approach |
Matches traffic against fixed rules and signatures. |
Utilizes WAF machine learning to identify anomalies and emerging attack patterns. |
| Accuracy |
Higher false positives often block legitimate users. |
Learns regular traffic, reducing false positives and improving accuracy. |
| Response Speed |
Requires manual updates for new threats and a more timely response. |
Responds in real time with AI firewall adaptive responses. |
| Scalability |
Struggles with heavy traffic, and rule evaluation adds overhead. |
Scales smoothly in high-volume apps without performance loss. |
| Zero-Day Defense |
Limited — relies on vendor updates to catch new exploits. |
Detects unusual behavior and blocks zero-day threats instantly. |
| Operational Impact |
More time spent tuning rules and investigating alerts. |
Cuts workload for teams, lowers costs, and supports compliance. |
| Business Value |
Provides basic protection but adds overhead. |
Drives ROI, builds trust, and strengthens long-term app security. |
Best Practices and Strategies for Implementing AI WAF
Rolling out an AI web application firewall is not a one-step job. It requires planning in four areas: deployment, integration, vendor selection, and ongoing management. If handled properly, the firewall improves security and reduces the workload for the team that operates it.
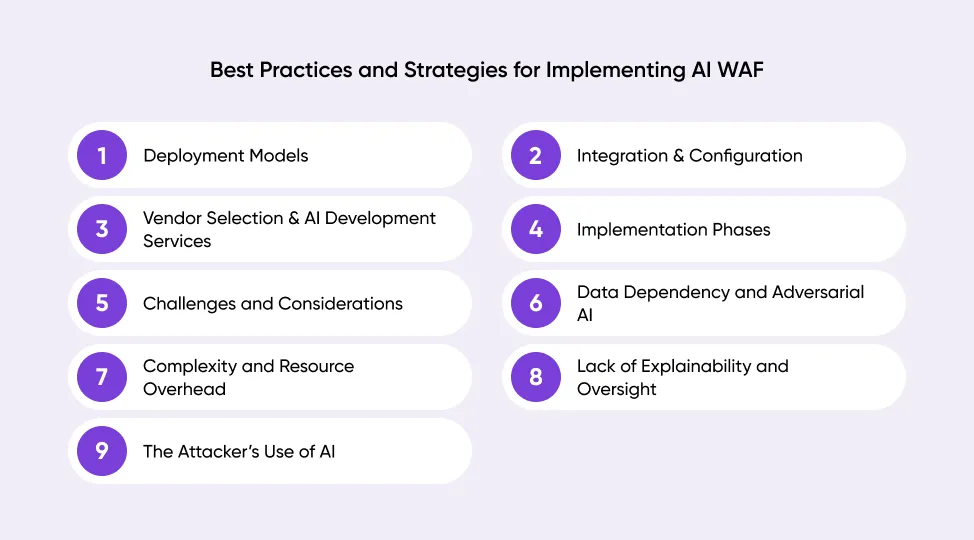
The practices outlined below provide guidance on implementing an AI WAF effectively and avoiding common problems during rollout.
Deployment Models
There’s no one-size-fits-all. The right setup depends on your environment.
- Cloud-Native: Ideal for businesses already in the cloud. It scales fast and requires less overhead.
- Hybrid: Works well for companies that still run part of their apps on-premise but want cloud flexibility.
- Edge Deployment: Places security closer to users, cutting delays and improving response time.
- API-First: Best for platforms that rely heavily on APIs, keeping those endpoints safe under heavy load.
Integration & Configuration
An AI WAF should blend into your stack, not fight with it.
- Test it with your existing apps before going live.
- Feed it good data so the models can actually learn what “normal” looks like.
- Tune settings carefully — too strict and you block good users, too loose and threats slip through.
- Track performance early; small bottlenecks grow if left unchecked.
Vendor Selection & AI Development Services
Choosing the right technology partner often matters more than the product itself.
- Pick a provider with real AI development services experience in security, not just marketing claims.
- Ask for case studies or customer stories, not just slide decks.
- Check how their models perform under pressure and how often they’re updated.
- Look for a partner who will support you after launch, not disappear once the contract is signed.
Implementation Phases
Rolling it out step by step avoids any misalignment
- Phase 1: Run AI WAF in monitoring mode first, learn traffic patterns without blocking users.
- Phase 2: Switch on AI features in test conditions with real traffic.
- Phase 3: Move into full deployment once you’re confident in the results.
- Phase 4: Continue tuning and adjusting — an AI WAF improves over time as it runs.
Challenges and Considerations
AI-based firewalls extend protection, but they also bring operational limits. These limits must be reviewed before deployment.
Data Dependency and Adversarial AI
Model accuracy depends on training data. Incomplete or biased data lowers detection rates. Attackers may inject false data or design adversarial inputs to bypass controls.
Complexity and Resource Overhead
AI systems require more resources than signature-based firewalls. Model training needs GPUs and qualified staff. High-volume inspection can also add latency.
Lack of Explainability and Oversight
Decisions made by deep models are not always transparent. Security teams may struggle to explain why traffic was blocked or allowed. Oversight is required for audits and investigations.
The Attacker’s Use of AI
Adversaries are adopting the same tools. AI is applied to automate intrusion attempts, generate malware variants, and optimize brute-force activity. Defenses must adjust continuously.
The Future of Web Application Security with AI
AI will continue to reshape how web application firewalls protect digital systems. The next phase will move beyond detection into more predictive and autonomous security functions.
Autonomous WAF Operations
Future AI WAFs will operate with less human input. Models will learn from live traffic, update defenses automatically, and adjust to new attack methods without waiting for rule changes.
Quantum-Resistant Security
As quantum computing develops, existing encryption may weaken. AI WAFs will integrate with quantum-resistant algorithms to protect sensitive transactions and data flows.
Integration with Zero-Trust Models
AI will help enforce zero-trust principles by validating every request and user action, rather than assuming trust once access is granted.
Edge AI Deployment
With applications moving closer to the edge, AI WAFs will also run at edge nodes. This reduces latency, speeds up detection, and scales protection for globally distributed apps.
Smarter Threat Intelligence
AI WAFs will merge local traffic data with global intelligence feeds. This will allow faster recognition of new attack campaigns, deliver stronger AI protection, and support better coordination across industries.
Quokka Labs: Leading the Charge in AI-Driven Security
Quokka Labs develops web applications with security built into the architecture. As a web app development company, it focuses on designing systems that remain reliable under high load and secure against common threats.
Projects are delivered for cloud, hybrid, and edge platforms, with a focus on compliance and performance requirements.
By combining engineering practice with applied research, Quokka Labs provides enterprise teams with systems that are both scalable and secure.
Their AI security services extend this work by supplying configuration support, monitoring, and ongoing model improvement for evolving environments.
Tags
AI solution
AI development
ai implementation
web application



 Facebook
Facebook
 Twitter
Twitter
 LinkedIn
LinkedIn
 Pinterest
Pinterest