Technology


9 min

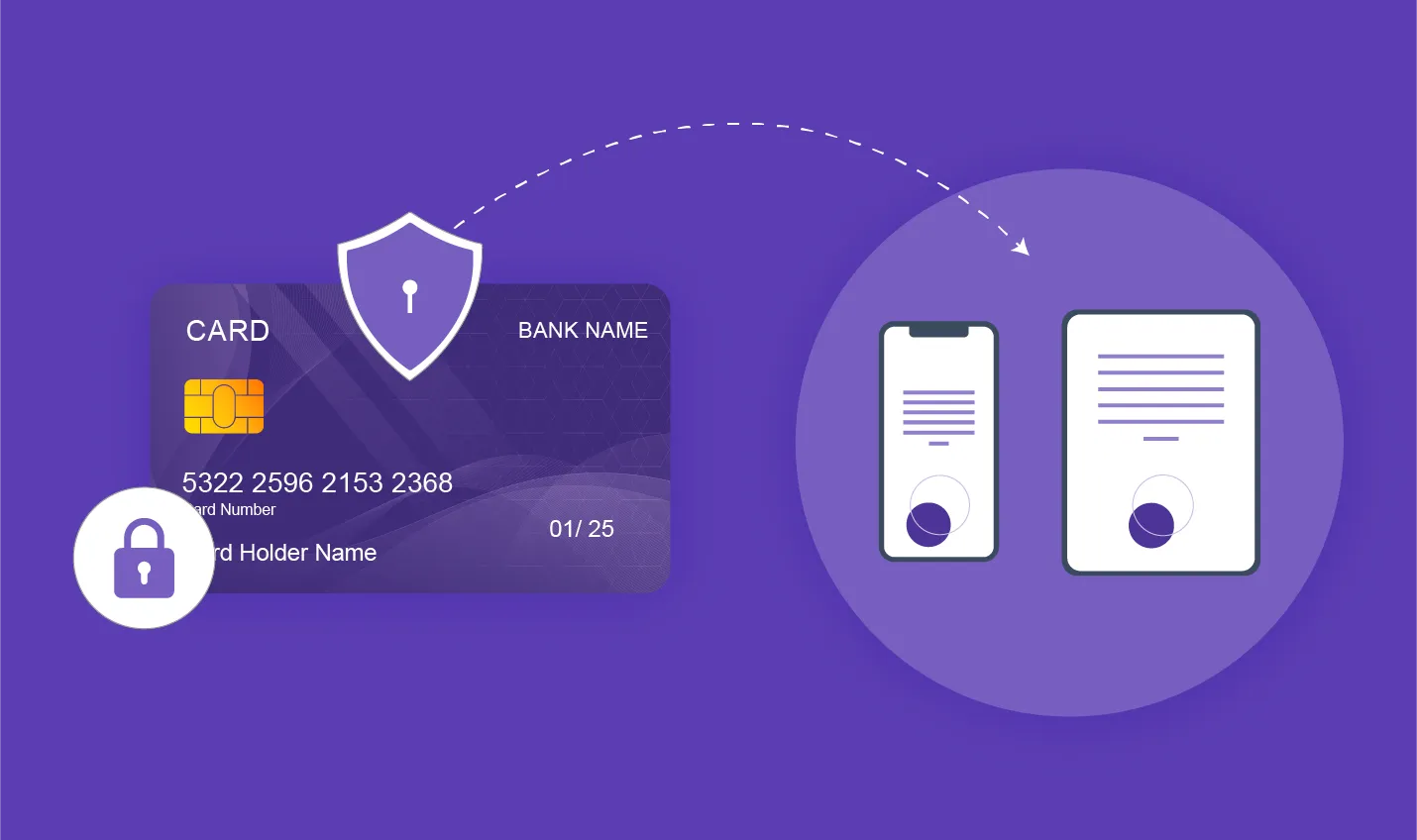
Tokenization replaces sensitive data with unique identification symbols that retain all the essential information about the data without compromising its security.

By Ayushi Shrivastava
31 Oct, 2022
All individuals or organizations have something that can’t be publicly exposed or shared. Thus to protect and invisiblize sensitive information, various practices have been launched.
Tokenization inherited the same thing. It scrambles the thing so that it can’t be accessible by an unauthorized person. This system swaps the original structure and value of data into a new format for the recipient.
Tokens are not a new or modern thing. In ancient times, tokens were available to purchase things. By the time we started using it to play video games. We now use it online to access the blockchain / metaverse. We have coins and tokens in a virtual format with a decentralized mechanism.
In the current era, these are storing valuable information, executing legal and financial transactions, and much more.
TrustCommerce first practiced the tokenization process. It is known for its software and payment delivery services. In 2021, TrustCommerce engaged with clients to isolate their card data/information. They were concerned about misuse & exposing sensitive information from merchant-end servers.
With this initiative, merchants cannot access the client’s card data. They have done a great job by aligning situational awareness. It has encouraged next-gen data privacy solution practices.
They devise a solution to convert the actual information into random number series launched as a token.
It is a process to convert valuable information and data into a more complex format so foolish attempts can’t unwrap it. It makes the data more rich, complex, and unattainable from unauthorized sources.
You can consider the token as a holder that is irreversible and undecipherable. There’s no change in value or context, resulting in everything being validated. We don’t need to disclose its scope.
Alternatively, It is a strategy to wrap an additional security layer or coverage for the business.
Tokens are considered to serve two different sides: By the People and By the System. One for front-end accessibility and another one for backend accessibility.
This category is far more challenging, where the individual has to know in- depth detail about the creation and launch. They must be familiar with the thin and thick points of mechanism that non-technical people can't understand.
It's all about system functionality and mechanism. Tokens are created or generated through the automotive system before the identifiers approach and interact with others.

It normalizes into 3 main common steps: Creation, Substitution, and Scramble & Store.
Instead of using any algorithm or computer concepts, a token is an entity created using the combination of numbers or letters. It’s organized through a set of rules and regularization. It possesses your participation in the process as an active member.
After the token creation, we move toward another step called Substitution. You can access the information and data with this token without exposing its actual value. It is exploited for multiple sessions also. And the system will not expose across any virtual channels and ecosystems.
The information will be encrypted in scrambled format and will store in an isolated space.
Modern world segmented tokenization in two manners: one is reversible, and another one is irreversible.
Reversible, as the term indicates, allows for reversing in the original value. These are available in formats, cryptographic and non-cryptographic
Cryptographic reversible tokens offer strong protection against risk and only store the encryption key.
Non-cryptographic reversible tokens stores cleartext data and generate a random value and equivalent tokens. In both scenarios, servers drive the request to inspect the value or randomly create the value and its corresponding token to manage the tokenization. The purpose is to check whether the value holds any cleartext or not.
Such lookup rounds increase the workload time amount of collisions. To manage these things, it increases the requirement of token servers so that reliability, load management, and downtime can manage.
Non-cryptographic tokenization is simply a vaultless process with random metadata for the token construction. There is no need for any synchronization or nearby connectivity, but scalability.
Irreversible tokens are the one that stays anonymous till the end, generalized as anonymization. Preferred in secondary environments to serve the production data, third-party analytics, and function-by-one-way method.
Evolution is coming, and tokenization is untouched by this fact. Organizations are taking the data privacy & security concept seriously. Thus, organizations are hunting for the best interactive solution for cyber theft and hackers to keep things miserable.
Tokenization is quite a trending concept these days. Everyone is familiar with and adapting to envelop the additional security for business. Although, companies & businesses sometimes find it complicated to manage token creation and arrangement.
No matter from which industry you come, tokenization will be worth it. It will organize and manage things more systematically and securely. Also, it will save you from unnecessary penalties across any channel. You can retrieve the information after decades from that application without extra effort. No time waste and no expensive resources are needed to store or maintain the data.
Automation and speed concepts are followed in our real world more frequently. So, why should it skip here? Tokens are serving the smooth, quick premium transaction applying the automation concept.
Data and information are easily accessible on the web. Hackers have many methods to catch and unbox these data sets. They know the worth of data better than us. They know how things can twist and utilize to fulfill their self- desires. Tokens are emerging as one of the secured assets to protect valuable information across the web ecosystem. It will annoy the hackers and restrict them from damaging the data and information available in the virtual world.
Retailers need a separate space to manage customers' data privacy and security. It can store the transaction details from their point of sale. For every business and organization, compliance assures robustness. Subsequently, PSI DSS has proposed a set of protocols to integrate tokenization . It is a far more affordable and easy-to-practice method for data security, transaction, and accessibility. It protects the debit card/ credit card and other bank account information. It is a modest, affordable, and efficient process to keep things enclosed.
Even if hackers get access to data, it is critical to bring back the information in a natural version.
Like every practice or technology, tokenization has some complexities. You must know you can’t rely only on this system to ensure data privacy & security. Encryption is a widespread practice and method to care for your data and information. Moreover, restrict the accessibility being exposed across unauthorized ecosystems or individuals.
You can find different software companies that can assist you in developing a dedicated system. It will protect your data and upgrade the organization's and users' security. Furthermore, it will extend the support to manage the security of phone numbers, mail addresses, banking info, debit card/ credit cards, personal information, etc.
Affordable Mobile App Development Without Quality Compromise
By Anupam Singh
8 min read
React vs React Native: Choosing the Right Framework for Your Project
By Ayushi Shrivastava
5 min read
What Is a Superapp? A New Era in Mobile App Development
By Dhruv Joshi
5 min read
Angular 18: Top Latest Features, Improvements and Updates
By Dhruv Joshi
5 min read

Technology


8 min
This blog explores how to achieve affordable mobile app development without compromising quality. It covers the rising demand for mobile apps with stats, the associated cost factors, and strategies for choosing affordable mobile development, such as the right development platform, leveraging pre-built solutions, outsourcing, agile methodology, focusing on MVP, optimizing resources, and investing in QA. The goal is to guide businesses in developing high-quality apps within budget.


Technology


5 min
Discover the differences between React and React Native to choose the best framework for your project. Explore features, development capabilities, and practical applications. Learn how Quokka Labs can guide you in your decision-making and customize solutions for mobile and web applications.


Technology


5 min
Explore the rise of superapps and their impact on mobile app development. This comprehensive guide tells you what superapps are, highlights top superapps in India, and explains how they benefit businesses. Learn about the development costs, key features, and future trends of superapps.

Feeling lost!! Book a slot and get answers to all your industry-relevant doubts